Shift5 Aircraft Network Security Program (ANSP) Compliance Module
Retain Records
Retain security log files for recordkeeping and compliance purposes.
Analyze Data
Conduct continuous or scheduled analysis of log files to detect anomalies.
Report Results
Report any anomalies or threats in a manner consistent with industry policies.
Verify Compliance
Verify compliance with a documented ANSP, and identify threats to the system.
Shift5 Aircraft Network Security Program (ANSP) Compliance Module
Shift5 is the only OEM- (original equipment manufacturer) agnostic platform that captures, analyzes, and reports anomalies in core network security log files automatically.
- Apply operator- and OEM-provided rulesets to the analysis of aircraft log files
- Identify and assess anomalies caused by human errors or malicious intent
- Prioritize events using our proprietary machine learning models based on the MITRE ATT&CK™ Framework
Description
More Products & Services
Products & Services
Shift5 GPS Integrity Module
Shift5
Enabled by one of the smallest, lightest, & lowest-power single pieces of hardware available. Operators and leaders still have little to no visibility into their vehicles' onboard data. Shift5 captures and analyzes serial bus data on the platform in real time, providing the anomaly detection and operational intelligence required to act.
Shift5's GPS Integrity Module is enabled by the Shift5 Manifold, a protocol-agnostic, U.S.-manufactured, configurable passive bus data-collecting computer engineered to fit within the ARINC 600 2 MCU form factor.
Using the data collected, translated, and streamed off-board the vehicle, Shift5 offers insights, providing real-time alerting and historical trends to assure mission readiness and cyber survivability. Our innovative technology enables military systems and commercial aviation, rail, and maritime vehicles to deny deception and ensure the integrity of GPS signals.
FEATURES
- Physics-Based Spoofing Detection helps determine if changes in position are physically possible, providing a simple yet effective method for initial spoofing detection.
- Advanced Detection Capabilities can analyze enriched data from all sources to detect subtle, sophisticated spoofing attempts, which is essential for identifying more complex spoofing strategies that might evade traditional detection spoofing techniques.
- Cockpit Alerting can provide real-time notifications to operators when the module detects GPS jamming or spoofing, helping ensure immediate awareness and faster response to potential threats.
- Seamless (SWaP Compliant) Integration with existing platforms, as well as the ability to deploy directly to onboard hardware if sufficient computing resources are available.
BENEFITS
- Enhanced Air Safety: By detecting GPS spoofing attempts, the Shift5 Platform can enhance the safety of military and commercial air operations, particularly in congested and contested areas.
- Sophisticated Detection Capabilities: Designed to use advanced algorithms to detect subtle, sophisticated spoofing attempts that might otherwise go unnoticed.
- Identification of Navigational Errors: By identifying spoofed GPS signals, the Platform helps prevent navigational errors that could lead to serious accidents or deviations from intended flight paths.
- Adaptability and Continuous Improvement: Designed for continuous refinement and improvement, the Shift5 Platform is continuously enhanced to adapt to new and evolving spoofing techniques.
- Operational Efficiency: By automating the detection process, the Shift5 Platform can reduce reliance on manual processes, enhancing operational efficiency.
- Integration into SOPs: Shift5 alerts can be integrated into existing Standard Operating Procedures (SOPs) to help preempt contamination of other POSNAV (Positioning and Navigation) data (e.g., Inertial Nav calibration against bad GPS data)
- Actionable Intelligence: Much like surface-to-air missile (SAM) sites are mapped for avoidance today, similar heat maps can be generated immediately using data captures and improved over time with additional detections to help operators avoid specific regions.
Shift5's GPS Integrity Module is enabled by the Shift5 Manifold, a protocol-agnostic, U.S.-manufactured, configurable passive bus data-collecting computer engineered to fit within the ARINC 600 2 MCU form factor.
Using the data collected, translated, and streamed off-board the vehicle, Shift5 offers insights, providing real-time alerting and historical trends to assure mission readiness and cyber survivability. Our innovative technology enables military systems and commercial aviation, rail, and maritime vehicles to deny deception and ensure the integrity of GPS signals.
FEATURES
- Physics-Based Spoofing Detection helps determine if changes in position are physically possible, providing a simple yet effective method for initial spoofing detection.
- Advanced Detection Capabilities can analyze enriched data from all sources to detect subtle, sophisticated spoofing attempts, which is essential for identifying more complex spoofing strategies that might evade traditional detection spoofing techniques.
- Cockpit Alerting can provide real-time notifications to operators when the module detects GPS jamming or spoofing, helping ensure immediate awareness and faster response to potential threats.
- Seamless (SWaP Compliant) Integration with existing platforms, as well as the ability to deploy directly to onboard hardware if sufficient computing resources are available.
BENEFITS
- Enhanced Air Safety: By detecting GPS spoofing attempts, the Shift5 Platform can enhance the safety of military and commercial air operations, particularly in congested and contested areas.
- Sophisticated Detection Capabilities: Designed to use advanced algorithms to detect subtle, sophisticated spoofing attempts that might otherwise go unnoticed.
- Identification of Navigational Errors: By identifying spoofed GPS signals, the Platform helps prevent navigational errors that could lead to serious accidents or deviations from intended flight paths.
- Adaptability and Continuous Improvement: Designed for continuous refinement and improvement, the Shift5 Platform is continuously enhanced to adapt to new and evolving spoofing techniques.
- Operational Efficiency: By automating the detection process, the Shift5 Platform can reduce reliance on manual processes, enhancing operational efficiency.
- Integration into SOPs: Shift5 alerts can be integrated into existing Standard Operating Procedures (SOPs) to help preempt contamination of other POSNAV (Positioning and Navigation) data (e.g., Inertial Nav calibration against bad GPS data)
- Actionable Intelligence: Much like surface-to-air missile (SAM) sites are mapped for avoidance today, similar heat maps can be generated immediately using data captures and improved over time with additional detections to help operators avoid specific regions.
Shift5 Cybersecurity Module
Shift5
Critical transportation and defense assets, such as military aircraft, maritime vessels, ground vehicles, weapon systems, commercial aircraft, and rolling stock, are extensive technology platforms that rely on a complex web of onboard operational technology (OT) components. These components, designed with a focus on reliability and under the presumption of use in an isolated operational environment, often lack sufficient cybersecurity protections.
Today, as OT components become increasingly interconnected with traditional IT systems and external networks, the absence of appropriate defenses creates a gap in cybersecurity that leaves critical assets precariously exposed to potential cyberattacks. Owners, operators, and maintainers must prioritize addressing this unchecked risk to keep their fleets protected.
Shift5’s unique platform is hardware, bus, and protocol agnostic, and can perform passive, full-take data capture from any onboard source — every frame, every bus, every protocol. The platform analyzes data in real-time to detect threats and unlock critical insights for cybersecurity teams, providing the depth and breadth of knowledge needed to understand and manage cybersecurity risks to today’s fleets and tomorrow’s next-gen assets.
BENEFITS
Cyber Resilience for Defense and Critical Transportation Fleets
Visibility
- Collect and Retain Every Frame of Onboard Data
- Uncover critical operational and cybersecurity insights by accessing, collecting, and retaining every frame of operational technology (OT) data.
- Overcome data collection challenges using a purpose-built platform designed to handle large volumes of data generated by defense and critical transportation assets.
Threat detection
- Analyze Onboard Data for Anomalies or Intrusions
- Effectively find and mitigate anomalies through continuous monitoring of onboard data.
- Improve detection rates by writing new signatures and rules for observed anomalies.
- Proactively detect new attack methods using advanced machine learning and analytics-based methods.
Alerting
- Alert on Suspicious Behavior in Real-Time
- Enhance situational awareness with real-time alerting on suspicious behavior.
- Enable proactive cyber defense by providing data for threat hunting, helping owners/operators mount a more comprehensive defense.
Automation
- Automate Incident Response and Mitigation
- Streamline incident management as real-time alerts trigger response plans and ticketing systems.
- Quickly troubleshoot and update compromised components with data-driven insights.
Today, as OT components become increasingly interconnected with traditional IT systems and external networks, the absence of appropriate defenses creates a gap in cybersecurity that leaves critical assets precariously exposed to potential cyberattacks. Owners, operators, and maintainers must prioritize addressing this unchecked risk to keep their fleets protected.
Shift5’s unique platform is hardware, bus, and protocol agnostic, and can perform passive, full-take data capture from any onboard source — every frame, every bus, every protocol. The platform analyzes data in real-time to detect threats and unlock critical insights for cybersecurity teams, providing the depth and breadth of knowledge needed to understand and manage cybersecurity risks to today’s fleets and tomorrow’s next-gen assets.
BENEFITS
Cyber Resilience for Defense and Critical Transportation Fleets
Visibility
- Collect and Retain Every Frame of Onboard Data
- Uncover critical operational and cybersecurity insights by accessing, collecting, and retaining every frame of operational technology (OT) data.
- Overcome data collection challenges using a purpose-built platform designed to handle large volumes of data generated by defense and critical transportation assets.
Threat detection
- Analyze Onboard Data for Anomalies or Intrusions
- Effectively find and mitigate anomalies through continuous monitoring of onboard data.
- Improve detection rates by writing new signatures and rules for observed anomalies.
- Proactively detect new attack methods using advanced machine learning and analytics-based methods.
Alerting
- Alert on Suspicious Behavior in Real-Time
- Enhance situational awareness with real-time alerting on suspicious behavior.
- Enable proactive cyber defense by providing data for threat hunting, helping owners/operators mount a more comprehensive defense.
Automation
- Automate Incident Response and Mitigation
- Streamline incident management as real-time alerts trigger response plans and ticketing systems.
- Quickly troubleshoot and update compromised components with data-driven insights.
Shift5 Predictive Maintenance Module
Shift5
Foresight, not hindsight: Unlock data-driven insights from data onboard critical transportation and defense assets.
BENEFITS
Observability
- Access, translate, and store onboard operational data and insights currently obscured by complexity or design.
- Monitor asset performance for patterns or trends indicating problems and identify potential maintenance actions.
Readiness
- Make better decisions — faster. Help to reduce unscheduled maintenance and optimize fleet availability.
- Enable maintenance scheduling at optimal intervals to reduce downtime, improve availability, and optimize resource use.
- Automate early warning indications to mitigate problems before they cause delays and identify resourcing needs earlier.
Safety
- Automate monitoring of system/component thresholds and help forecast and prevent equipment failure.
- Perform scheduled maintenance before equipment failure to help reduce the risk of malfunction.
- Identify and prioritize potential safety hazards which can avoid legal liabilities and fines.
Cost savings
- Identify equipment failures and accurately attribute maintenance responsibilities.
- Help ensure assets remain in service longer to prevent costly delays and lost revenue.
- Prioritize maintenance for equipment likely to fail to help reduce costs.
- Find and fix potential safety hazards which can mitigate legal liabilities and fines.
- Keep asset components at optimal performance levels to help extend asset life.
BENEFITS
Observability
- Access, translate, and store onboard operational data and insights currently obscured by complexity or design.
- Monitor asset performance for patterns or trends indicating problems and identify potential maintenance actions.
Readiness
- Make better decisions — faster. Help to reduce unscheduled maintenance and optimize fleet availability.
- Enable maintenance scheduling at optimal intervals to reduce downtime, improve availability, and optimize resource use.
- Automate early warning indications to mitigate problems before they cause delays and identify resourcing needs earlier.
Safety
- Automate monitoring of system/component thresholds and help forecast and prevent equipment failure.
- Perform scheduled maintenance before equipment failure to help reduce the risk of malfunction.
- Identify and prioritize potential safety hazards which can avoid legal liabilities and fines.
Cost savings
- Identify equipment failures and accurately attribute maintenance responsibilities.
- Help ensure assets remain in service longer to prevent costly delays and lost revenue.
- Prioritize maintenance for equipment likely to fail to help reduce costs.
- Find and fix potential safety hazards which can mitigate legal liabilities and fines.
- Keep asset components at optimal performance levels to help extend asset life.
The Shift5 Platform
Shift5
Shift5 built a unique model that brings order and clarity to the complexity of onboard data flowing from commercial aerospace, rail, and defense fleets and weapon systems. Our platform captures and analyzes real-time serial bus data, revealing critical operational and cybersecurity insights that enable organizations to move from data to decisions quickly and confidently. Shift5 unlocks the complete ecosystem of onboard data for operations, maintenance, and cybersecurity teams for the first time, enabling real-time decision intelligence through complete onboard data access and observability from the asset level to fleet scale. Shift5 delivers modern OT solutions for the security, availability, safety, resilience, and reliability of today’s fleets and tomorrow’s next-gen assets.
CORE PRODUCT MODULES
- Cybersecurity Module: Detects, identifies, and generates alerts foron new anomalous activities and known threats, providing real-time notifications that can enable faster response and proactive mitigation of potential cybersecurity risks.
- Predictive Maintenance Module: Provides real-time, data-driven insights needed to predict and schedule maintenance effectively, helping to avoid critical failures before they happen and to ensure the safety and performance of critical transportation and defense fleets.
- Compliance Module: Automates compliance efforts for onboard fleet data by helping to ensure that it is processed, managed, and stored in accordance with regulatory requirements and industry best practices.
- GPS Integrity Module: Provides sophisticated, multi-faceted detection and alerting for GPS spoofing attempts, helping to ensure the safety and reliability of navigation.
BENEFITS
Observability
- Collect and retain every frame of onboard data created by commercial and defense fleets and weapon systems.
- Access, translate, analyze, contextualize, store, and action onboard operational data and insights currently obscured by complexity or design.
- Monitor fleet performance for patterns or trends indicating problems and identify potential maintenance, security, or compliance actions.
Decision Intelligence
- Transform onboard data into continually improving decision intelligence with critical contextual insights and actionable analytics at the edge that enable predictive and retrospective analysis.
- Identify events that may be leading indicators of an equipment failure or cyber threat.
- Reduce decision latency with actionable real-time cybersecurity, maintenance, and compliance dashboards.
- Make critical mission and business decisions with clarity and context based on real-time data across every asset and every fleet.
Cybersecurity
- Detect, identify, and alert in real-time on anomalous behavior and enable teams to take action to mitigate cybersecurity risks.
- Apply rules-based detection with advanced machine learning and analytics-based methods to enable real-time detection of threats like unauthorized software configurations and cyber anomalies in onboard networks.
- Conduct faster, more accurate incident response, intrusion detection and prevention using retrospective data analysis, enabling a fuller understanding of a bad actor's tactics, techniques, and procedures.
Availability
- Make smarter decisions — faster. Reduce unscheduled maintenance and optimize fleet availability.
- Enable maintenance scheduling at optimal intervals to reduce downtime, improve availability, and optimize resources.
- Automate early warning indications to mitigate problems before they cause delays and identify resourcing needs earlier.
- Mitigate degraded operational environments by addressing fleet and weapon systems maintenance issues in real-time.
Safety
- Automate monitoring of system/component thresholds and help forecast and prevent equipment failure.
- Help ensure the safety of crew, passengers, and cargo, prevent legal liabilities, and avoid penalties by identifying and prioritizing potential safety hazards.
Resilience
- Respond quickly to evolving cyber threats and changing operational conditions, minimizing downtime and maintaining asset and fleet readiness.
- Help ensure assets can sustain operations safely, even in the face of potential equipment failure, cyber threats, or other disruptions.
- Conduct thorough risk assessments to identify vulnerabilities and develop effective mitigation strategies like improved operating procedures and contingency planning.
Reliability
- Reduce the risk of component failures and help improve the safety and security of passengers, personnel, and cargo.
- Ensure consistent and predictable asset operation, decreasing delays and enabling smooth, efficient operations.
- Increase asset availability by using data-driven analytics to optimize maintenance schedules.
Cost Savings
- Detect and mitigate cyber threats that could degrade or severely limit the ability to maintain fleet operations.
- Identify equipment failures before they happen, accurately attribute root causes, and allocate resources.
- Optimize maintenance schedules to help ensure fleets and weapon systems remain in service longer and prevent costly delays and lost revenue.
- Extend the value and utility of existing cyber, maintenance, and compliance solutions by enriching them with additional OT asset intelligence.
CORE PRODUCT MODULES
- Cybersecurity Module: Detects, identifies, and generates alerts foron new anomalous activities and known threats, providing real-time notifications that can enable faster response and proactive mitigation of potential cybersecurity risks.
- Predictive Maintenance Module: Provides real-time, data-driven insights needed to predict and schedule maintenance effectively, helping to avoid critical failures before they happen and to ensure the safety and performance of critical transportation and defense fleets.
- Compliance Module: Automates compliance efforts for onboard fleet data by helping to ensure that it is processed, managed, and stored in accordance with regulatory requirements and industry best practices.
- GPS Integrity Module: Provides sophisticated, multi-faceted detection and alerting for GPS spoofing attempts, helping to ensure the safety and reliability of navigation.
BENEFITS
Observability
- Collect and retain every frame of onboard data created by commercial and defense fleets and weapon systems.
- Access, translate, analyze, contextualize, store, and action onboard operational data and insights currently obscured by complexity or design.
- Monitor fleet performance for patterns or trends indicating problems and identify potential maintenance, security, or compliance actions.
Decision Intelligence
- Transform onboard data into continually improving decision intelligence with critical contextual insights and actionable analytics at the edge that enable predictive and retrospective analysis.
- Identify events that may be leading indicators of an equipment failure or cyber threat.
- Reduce decision latency with actionable real-time cybersecurity, maintenance, and compliance dashboards.
- Make critical mission and business decisions with clarity and context based on real-time data across every asset and every fleet.
Cybersecurity
- Detect, identify, and alert in real-time on anomalous behavior and enable teams to take action to mitigate cybersecurity risks.
- Apply rules-based detection with advanced machine learning and analytics-based methods to enable real-time detection of threats like unauthorized software configurations and cyber anomalies in onboard networks.
- Conduct faster, more accurate incident response, intrusion detection and prevention using retrospective data analysis, enabling a fuller understanding of a bad actor's tactics, techniques, and procedures.
Availability
- Make smarter decisions — faster. Reduce unscheduled maintenance and optimize fleet availability.
- Enable maintenance scheduling at optimal intervals to reduce downtime, improve availability, and optimize resources.
- Automate early warning indications to mitigate problems before they cause delays and identify resourcing needs earlier.
- Mitigate degraded operational environments by addressing fleet and weapon systems maintenance issues in real-time.
Safety
- Automate monitoring of system/component thresholds and help forecast and prevent equipment failure.
- Help ensure the safety of crew, passengers, and cargo, prevent legal liabilities, and avoid penalties by identifying and prioritizing potential safety hazards.
Resilience
- Respond quickly to evolving cyber threats and changing operational conditions, minimizing downtime and maintaining asset and fleet readiness.
- Help ensure assets can sustain operations safely, even in the face of potential equipment failure, cyber threats, or other disruptions.
- Conduct thorough risk assessments to identify vulnerabilities and develop effective mitigation strategies like improved operating procedures and contingency planning.
Reliability
- Reduce the risk of component failures and help improve the safety and security of passengers, personnel, and cargo.
- Ensure consistent and predictable asset operation, decreasing delays and enabling smooth, efficient operations.
- Increase asset availability by using data-driven analytics to optimize maintenance schedules.
Cost Savings
- Detect and mitigate cyber threats that could degrade or severely limit the ability to maintain fleet operations.
- Identify equipment failures before they happen, accurately attribute root causes, and allocate resources.
- Optimize maintenance schedules to help ensure fleets and weapon systems remain in service longer and prevent costly delays and lost revenue.
- Extend the value and utility of existing cyber, maintenance, and compliance solutions by enriching them with additional OT asset intelligence.
Description
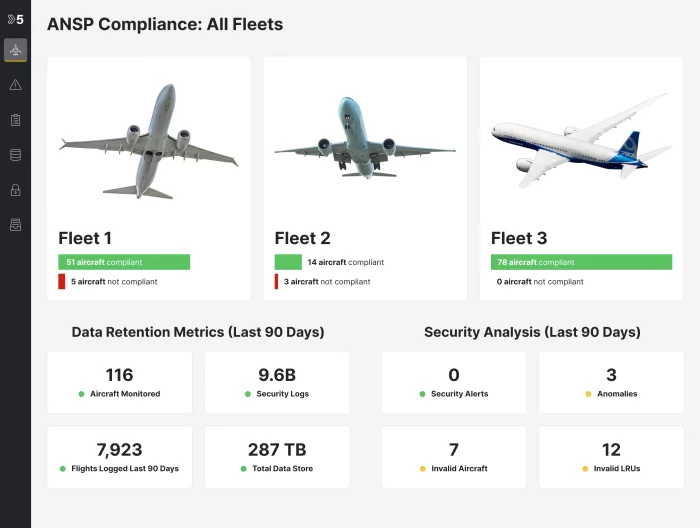
The Shift5 Compliance Module automates compliance efforts for data created on board fleet aircraft. Developed in partnership with aviation industry experts, enables automation of the Federal Aviation Administration’s (FAA) guidelines in Advisory Circular (AC) 119-1 requiring operators to create an Aircraft Network Security Program (ANSP).
AC 119-1’s ANSP requirements are intended to help operators address credible cyber threats and potential critical safety issues, but they don’t provide clear guidance on operationalizing them, frequently leaving operators struggling to find a straightforward path to compliance. The Shif5 Compliance Module facilitates automated rules-based log file analysis, helping make compliance easier, faster, and more efficient so operators can focus on enhancing the safety and cybersecurity of connected aircraft.
The module collects log files using existing aircraft data offloading processes, so there’s no additional hardware required to get started. It can also be deployed as a managed service, offering greater flexibility for teams to focus on other crucial tasks.
Reduce the workload for security teams and more.
Over 60% of cybersecurity leaders say their teams are understaffed, making process automation more critical than ever. The Shift5 platform automatically collects, analyzes, and correlates data from each aircraft to provide better observability across the entire fleet.
Normalize log file data across different platforms.
Data in log files and its formatting can vary widely across aircraft manufacturers, platforms, and even between similar aircraft. The Shift5 platform unpacks log files and automatically normalizes the data in them into a consistent format. This automation eliminates the need for teams to stitch together inconsistent data sets. It also enables the platform to quickly identify commonalities in fleet analysis globally, which improves the robustness and accuracy of the platform for all Shift5 customers.
Focus on the security events that matter most.
A single aircraft can log countless events, making manual assessment and prioritization of risks virtually impossible. Information about critical anomalies must also be made available to regulators and industry experts without delay to ensure flight safety.
When the Shift5 platform identifies a suspicious or malicious event, it assesses its impact quantitatively based on techniques in the MITRE ATT&CK™ Framework. The platform also makes it easy to package and export analysis and assessments from the Shift5 console for internal team review and prompt regulatory reporting.
AC 119-1’s ANSP requirements are intended to help operators address credible cyber threats and potential critical safety issues, but they don’t provide clear guidance on operationalizing them, frequently leaving operators struggling to find a straightforward path to compliance. The Shif5 Compliance Module facilitates automated rules-based log file analysis, helping make compliance easier, faster, and more efficient so operators can focus on enhancing the safety and cybersecurity of connected aircraft.
The module collects log files using existing aircraft data offloading processes, so there’s no additional hardware required to get started. It can also be deployed as a managed service, offering greater flexibility for teams to focus on other crucial tasks.
Reduce the workload for security teams and more.
Over 60% of cybersecurity leaders say their teams are understaffed, making process automation more critical than ever. The Shift5 platform automatically collects, analyzes, and correlates data from each aircraft to provide better observability across the entire fleet.
Normalize log file data across different platforms.
Data in log files and its formatting can vary widely across aircraft manufacturers, platforms, and even between similar aircraft. The Shift5 platform unpacks log files and automatically normalizes the data in them into a consistent format. This automation eliminates the need for teams to stitch together inconsistent data sets. It also enables the platform to quickly identify commonalities in fleet analysis globally, which improves the robustness and accuracy of the platform for all Shift5 customers.
Focus on the security events that matter most.
A single aircraft can log countless events, making manual assessment and prioritization of risks virtually impossible. Information about critical anomalies must also be made available to regulators and industry experts without delay to ensure flight safety.
When the Shift5 platform identifies a suspicious or malicious event, it assesses its impact quantitatively based on techniques in the MITRE ATT&CK™ Framework. The platform also makes it easy to package and export analysis and assessments from the Shift5 console for internal team review and prompt regulatory reporting.

Share
Recent Chats
Share via email
Future: handle WhatsApp here
Future: handle LinkedIn here
Future: handle Twitter here
SUBMENU HERE
Share via Chat
Copy Link

